Why Is 2^256 Secure?
There’s always a lot of talk about the security of modern cryptographic hash functions, mainly SHA-256. This is a hash function used to verify a lot of important stuff – modern website logins are hashed with it and Bitcoin relies on it almost entirely. Some popular VPN services tend to use SHA-512 for encryption, going even further to secure their networks.
There’s always a lot of confusion regarding the safety of the function – as we know in the past things are found to be insecure after being declared ‘absolutely secure’ a few years prior to them being broken. Why is this particular iteration of hash functions so perfect?
The main problem with this idea is how poorly the human mind can understand the exponential function. Our brains can wrap around the concepts of addition and multiplication fine – but when we get to exponents our minds have trouble wrapping our heads around how quickly numbers get unimaginably big.
So what exactly is 2^256? Well, if we’re being technical…
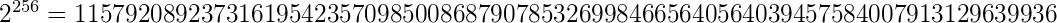
So – for all those doubting the security of 2^256 collision chances, there’s the number: There is a 1 in over 115 quattuorvigintillion (that’s a 78 digit number) chance of finding a collision.
This number is bigger than the number of atoms in the perceivable universe. And not by just a little bit either. Exponentially bigger. This number is so big that the human mind can’t comprehend how big it is. It’s just really big. Huge. I can not overstate this enough. This is a very big number. Your financial and cryptographic transactions are secure because of how big this is. Only a fool would attempt to brute force this many possible combinations.
So why is this particular number now big enough to be secure for the significant future? Well, it’s partly because we’ve simply increased the exponent to the point where the numbers get ridiculous, whereas before (with hash functions such as MD5, we were being a little cautious with a ‘just enough’ approach to exponential security and an underestimation of how fast computing speed could get.
A brute force attack on with this many combinations is, however, quite infeasible. Does that mean it’s impossible for someone to find the same hash as someone else? No. It’s not mathematically impossible. It never will be – that’s how numbers work. If a number exists, anyone can find it. However, at this point it’s no longer worth your time trying – because it would take hundreds of millions of years to maybe get a result.
Is it technically, for the sake of mathematics, possible? Yes. Will we ever witness it in a meaningful way?
